

The IoT Boom and Its Security Challenges
The rise of IoT devices is transforming our digital landscape, with experts projecting 30.9 billion devices by 2025. (Cyber Management Alliance) This rapid growth brings significant security risks.
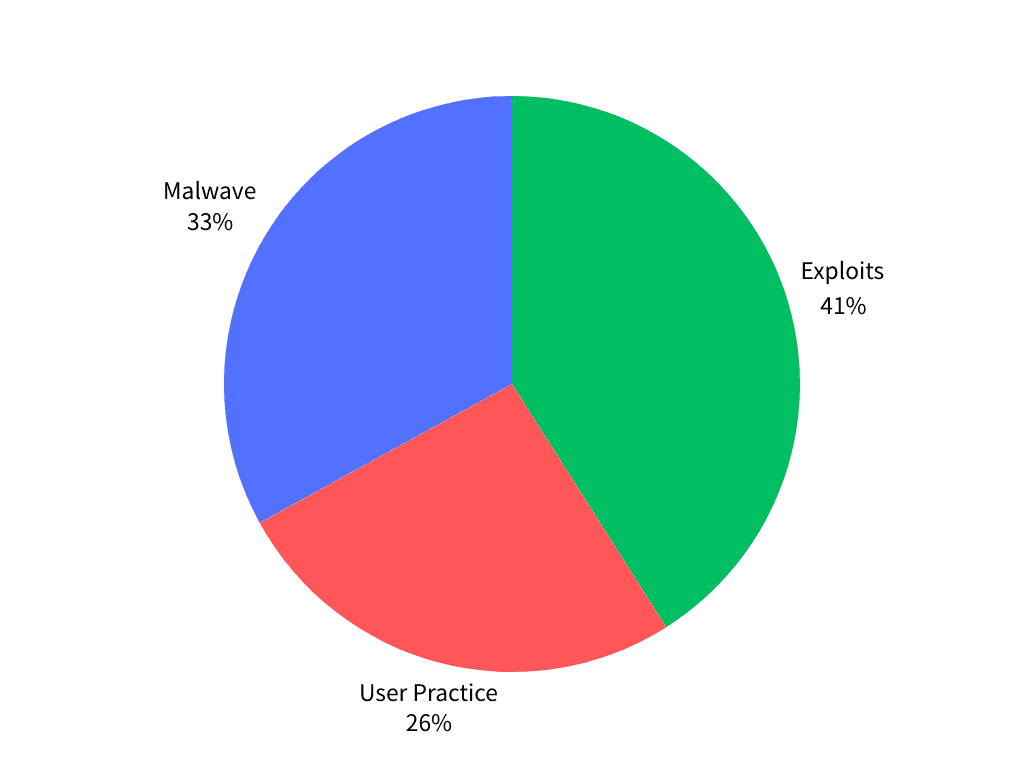
(IoT Security Concerns: Recent Research Pie Chart)
Recent research highlights critical IoT security concerns (Palo Alto Networks):
- 57% of IoT devices are vulnerable to medium- or high-severity attacks.
- 98% of IoT device traffic is unencrypted.
- Top threats include exploits (41%), malware (33%), and user practice issues (26%).
Other research findings (Bitdefender):
Only 20% of board members are “highly engaged” in cybersecurity matters, despite 80% expecting a breach.
For audio products, unauthorized access to devices could lead to eavesdropping or manipulation. While data breaches might expose sensitive information like voice commands and user preferences. These devices are also vulnerable to botnet recruitment, potentially participating in larger cyberattacks without users’ knowledge. Firmware vulnerabilities and the emerging threat of voice spoofing attacks further compound these concerns, highlighting the complex security challenges facing the audio IoT sector.
These multifaceted threats underscore the urgent need for enhanced IoT cybersecurity measures, especially in the audio industry. Recognizing this pressing issue, regulatory bodies are taking action. This regulatory shift signals a growing awareness of IoT vulnerabilities and the need for manufacturers to prioritize security from the ground up.
The European Commission Steps Up
In response to these global concerns, the European Commission has made a game-changing move by implementing the Radio Equipment Directive – Delegated Act (RED-DA) and EN 303 645. These requirements establish a new gold standard for security. We’re talking about frequent vulnerability checks and firmware updates that audio product companies across the world must implement to access the European market.
Compliance is urgent
The clock is ticking toward the August 2025 compliance date, which emphasizes the feasibility and importance of prompt action. For production and manufacturing, this deadline is more than just a regulatory challenge; it is a critical point in aligning with global standards, ensuring the security and trustworthiness of their IoT services in an increasingly security-conscious market.
To navigate these challenges, Jazz Hipster’s QA experts offer comprehensive guidance on essential cybersecurity practices for audio products, helping protect your devices and customers in this evolving landscape.

What is RED-DA?
Definition and Origins
RED Delegated Act (RED-DA) is the European Union’s answer to the growing cybersecurity threats facing our increasingly connected world. Think of it as a rulebook designed to protect radio and wireless devices from cyber-attacks. With so many devices talking to each other, the EU decided it was time to lay down some strict security guidelines to keep both consumers and industrial users safe from cyber vulnerabilities.
RED-DA Activation
So, how did this all come about? On October 29, 2021, the European Commission activated Articles 3.3 (d), (e), and (f) of the RED Directive by adopting the RED Delegated Act. This wasn’t just a back-office update; it was a big deal and was published in the Official Journal of the European Union on January 12, 2022.
Here’s what these key articles are all about:
- Article 3.3(d): Ensures that radio equipment does not harm the network or its functioning nor misuses network resources, thereby preventing unacceptable service degradation.
- Article 3.3(e): Mandates that radio equipment incorporates safeguards to protect the personal data and privacy of both the user and the subscriber.
- Article 3.3(f): Requires radio equipment to support features ensuring protection from fraud.
Key Aspects of RED-DA
RED-DA focuses on several critical articles aimed at enhancing cybersecurity protocols. Article 3.3.d requires all devices to implement authentication and data encryption methods to safeguard user data from unauthorized access. Article 3.3.e mandates that devices must be able to withstand common types of cyber-attacks, ensuring continuous functionality and service. Lastly, Article 3.3.f emphasizes the need for devices to have capabilities to maintain user privacy even in the event of a system compromise.
Mandatory Compliance by August 2025
These specific provisions of the RED-DA are set to become mandatory starting August 1, 2025. Compliance with these articles is crucial for production and manufacturing to continue selling their products within the EU market, emphasizing the need for timely adaptation to these regulatory standards.
Special Considerations for Audio Products
Audio Products face unique challenges and opportunities under RED-DA. The dual nature of audio devices as both consumer and professional tools exposes them to specific cyber threats, such as firmware tampering or unauthorized access via connected services. However, compliance with RED-DA mitigates these risks and serves as a competitive edge. An Audio manufacturer like Jazz Hipster’s long-standing reputation for quality and reliability is enhanced by proactive adherence to these new cybersecurity standards.
One-Stop Service Advantage
Jazz Hipster understands that achieving compliance swiftly and efficiently is crucial in today’s competitive environment. That’s why we offer comprehensive one-stop services, covering everything from design to testing and certification. Our holistic approach ensures that your products meet RED-DA and EN 303 645 standards. We streamline the path to compliance, saving you time and reducing costs. This integrated service model positions Jazz Hipster as a trusted partner in navigating the complexities of regulatory compliance.
What is EN 303 645?
Detailed Security Requirements
EN 303 645 is instrumental in laying down technical guidelines that directly align with the RED Delegated Act’s objectives. Focusing on mitigating vulnerabilities inherent in the IoT landscape.
- Authentication Protocols: The standard mandates that devices implement authentication mechanisms, going beyond the elimination of default passwords. This includes the management of authentication data and the implementation of ‘minimum security mechanisms’ as specified in the ETSI document. These mechanisms ensure that user credentials are securely handled and stored, significantly reducing the risk of unauthorized access. The standard emphasizes the use of multi-factor authentication where appropriate and the implementation of secure password policies.
- Secure Data Storage and Transmission: The standard emphasizes the importance of securing data both at rest and in transit. Encryption protocols must be applied to protect sensitive user data from being intercepted, altered, or misused as it moves across networks or while stored on devices.
- Privacy Controls and Data Minimization: EN 303 645 emphasizes the principle of ‘data minimization’ alongside robust privacy controls. The standard requires that devices collect and process only the personal data necessary for their intended functionality. It mandates clear user consent mechanisms before any personal data collection, and provides users with effective tools to manage the collection, processing, and sharing of their data. Manufacturers are encouraged to design their devices with privacy in mind, implementing features that allow users to easily delete their personal data and to understand what data is being collected and why.
- Secure Software Updates and Vulnerability Management: EN 303 645 emphasizes the critical importance of a ‘secure update process’. Manufacturers are required to provide timely updates to address security vulnerabilities, ensuring these updates are delivered securely to users. The standard mandates mechanisms to verify the integrity and authenticity of updates, and requires clear communication to users about the update process and its importance. This secure update process is crucial for maintaining the long-term security and functionality of IoT devices, especially as new threats emerge. The standard also encourages manufacturers to provide clear policies on the duration of software update support for their devices.
- Network Security Features: EN 303 645 requires devices to implement network security measures that prevent them from becoming part of botnets or being used in DDoS attacks. This includes capabilities like intrusion detection systems and the ability to respond to network anomalies in real-time.
Detailed Implementation Guides and Testing Standards
- TS 103 701: This document provides comprehensive guidelines for testing and verifying the conformity of IoT devices with the EN 303 645 standard. It helps ensure consistency and thoroughness in the assessment of device security, specifying the methods and criteria testing laboratories should use. This structured approach greatly assists manufacturers in preparing their products for regulatory compliance, ensuring all aspects of security are adequately covered.
- TR 103 621: Serving as an implementation guide, TR 103 621 offers practical advice for manufacturers on how to implement the necessary security measures to comply with EN 303 645. It acts as a valuable resource during the product development and testing phases, helping manufacturers understand and apply the standard’s requirements effectively. This guide discusses best practices and provides actionable steps for aligning product design and procedures with the required security outcomes.
By utilizing these documents, manufacturers can achieve a clear understanding of the assessment criteria and implementation steps necessary for compliance. Also, it’s important to note that the current version of EN 303 645 referenced in this article is V2.1.1, published in June 2020. However, standards are subject to regular reviews and updates. Manufacturers and stakeholders are strongly advised to regularly check the ETSI website for any updates or revisions to the standard. Staying informed about the latest version ensures ongoing compliance and helps in adapting to evolving cybersecurity requirements in the rapidly changing IoT landscape.
Impact of Compliance
Adhering to EN 303 645 aligns with regulatory requirements and significantly boosts consumer confidence in IoT products. By meeting these standards, manufacturers demonstrate their commitment to protecting consumer privacy and enhancing the security of their devices, which can be a significant market differentiator in an increasingly security-conscious world.

Preparing for Compliance
Overview of Compliance Methods
- Self-Assessment: Manufacturers can conduct self-assessments to ensure their products meet the required harmonized standards. This process involves internal checks and thorough documentation to verify that all design and functional aspects of the products align with specified security protocols.
- Third-Party Assessment: For an unbiased evaluation, manufacturers have the option to utilize independent testing organizations. These organizations assess product compliance with cybersecurity standards, providing an external validation of security measures.
Conformity Assessments and Certification
- Conformity Assessment Process: Once harmonized standards are established, laboratories conduct conformity assessments to certify that products meet all the regulatory requirements. This process ensures that products being introduced to the market are compliant with EU standards.
- EU Type Examination Certificate (EU-TEC): This certificate is crucial for manufacturers as it validates that a product has passed all necessary EU compliance checks. Obtaining an EU-TEC is essential for entering the EU market, as it assures that the product meets stringent EU cybersecurity and safety standards.
Detailed Conformity Assessment Process
To comply with EN 303 645 and related standards, manufacturers must engage in a detailed conformity assessment process. This process ensures the thorough validation and certification of products, demonstrating that they meet stringent cybersecurity requirements.
- Implementation Conformance Statement (ICS): The Implementation Conformance Statement (ICS) is a critical document detailing the specific security measures implemented in the Device Under Test (DUT). It provides insight into its compliance with mandatory and recommended requirements, including:
- Functionalities Implemented: Descriptions of the security features and functionalities incorporated into the product.
- Compliance Details: Clarifications on how the DUT meets mandatory, recommended, and conditional requirements outlined by EN 303 645.
- Supporting Evidence: Documentation of tests, audits, and practices demonstrating compliance with security measures.
- Implementation eXtra Information for Testing (IXIT): The Implementation eXtra Information for Testing (IXIT) form outlines the design, implementation methods, and technical details of the DUT. It informs testing laboratories about the product’s functionalities and testing requirements, covering:
- Functionalities Implemented: Descriptions of the security features and functionalities incorporated into the product.
- Compliance Details: Clarifications on how the DUT meets mandatory, recommended, and conditional requirements outlined by EN 303 645.
Supporting Evidence: Documentation of tests, audits, and practices demonstrating compliance with security measures.
Strategic Recommendations for Manufacturers
- Choosing the Right Assessment Method: Manufacturers should consider the complexity of their products and their specific market goals when deciding between self-assessment and third-party assessment. Factors such as product complexity, market reach, and internal capabilities to manage compliance processes influence this decision.
- Preparing for Assessment: To ensure a smooth assessment process, manufacturers need to gather all necessary documentation and align their operations with best practices in cybersecurity. This includes maintaining detailed records of security measures, update logs, and compliance efforts.
Impact on Manufacturers
The impact of RED-DA and EN 303 645 on manufacturers, especially within the audio manufacturing sector, is multifaceted. These regulations affect production processes, market positioning, and regulatory compliance.
- Broader Industry Impact: Compliance with these regulations is not merely a legal obligation but also a significant competitive advantage in the marketplace. Manufacturers that meet these standards can leverage their compliance as a key selling point, promoting their commitment to security and reliability.
- Urgency for Preparation: Given the impending 2025 deadline for mandatory compliance, manufacturers must begin their preparations now to avoid disruptions. This involves updating internal processes, training staff, and potentially re-engineering products to meet the stringent security requirements.
- Cost Implications: While adapting to these regulations incurs costs, particularly in the short term, the long-term benefits of compliance—such as reduced risk of cyber incidents and stronger market trust—can outweigh these initial investments.
Act Now for Compliance and Competitive
Key Takeaways
- Urgency of Compliance: With the August 2025 deadline approaching, manufacturers must act promptly to ensure they meet the new standards.
- Comprehensive Security Measures: The new standards demand security considerations from the design phase, encompassing authentication, encryption, privacy protection, and more.
- Market Competitive Advantage: Early compliance can serve as a significant differentiator in an increasingly security-conscious market.
- Long-term Industry Impact: These regulations will drive innovation in cybersecurity practices, potentially leading to safer and more reliable IoT ecosystems.
Looking Ahead
We can expect to see a surge in cybersecurity-focused innovations. Manufacturers who view these regulations not as obstacles but as opportunities for improvement will likely emerge as leaders in the new, security-prioritized landscape.
For companies like Jazz Hipster, this regulatory shift presents a chance to reinforce their commitment to quality and security. While the path to compliance may be challenging, it is an essential journey that will ultimately benefit audio industries, consumers, and the broader IoT ecosystem. The future of connected devices is secure, and the time to prepare for that future is now.
References
- [1] Cyber Management Alliance – IoT Security: 5 cyber-attacks caused by IoT security vulnerabilities – https://www.cm-alliance.com/cybersecurity-blog/iot-security-5-cyber-attacks-caused-by-iot-security-vulnerabilities
- [2] Palo Alto Networks – Unit 42 IoT Threat Report 2020 – https://unit42.paloaltonetworks.com/iot-threat-report-2020/
- [3] ETSI – EN 303 645 V2.1.1 (2020-06) – https://www.etsi.org/deliver/etsi_en/303600_303699/303645/02.01.01_60/en_303645v020101p.pdf
- [4] OnwardSecurity – RED-DA Certification Service – https://www.onwardsecurity.com/lab_security-detail/redda/
- [5] UL Solutions – Cybersecurity Advisory for RED Compliance – https://www.ul.com/services/ul-solutions-cybersecurity-advisory-red-compliance
- [6] Bitdefender – IoT-related data breaches on the rise, research shows – https://www.bitdefender.com/blog/hotforsecurity/iot-related-data-breaches-rise-research-shows/




